Thursday, December 27, 2007
CMPC Testers Needed!
previously.
NOTE: Testing completed. Thanks to all. Release coming soon!
-Mike
Sunday, December 23, 2007
CS-MARS Generation 1 EOL/EOS Announcement
-Mike
Friday, December 21, 2007
Cisco NAC Appliance 4.1(3) Released
- New web agent for client scanning
- Enhanced HA support (fixes the ARP issue of switching IPs it seems)
- Enhanced guest access option (policy acceptance and flexible ID fields)
- OOB enhancement for VoIP environments
Get downloading!
-Mike
Thursday, December 20, 2007
CS-MARS Package Checker (CMPC) Broken!
-Mike
Wednesday, July 04, 2007
CS-MARS Package Checker (CMPC) v1.2 Released!
- Re-written to no longer run as a command line executable (no more black box popping up!)
- Added the following package options for notifications:
- Cisco Adaptive Secuirty Appliance OS and Device Manager
- Cisco PIX Secuirty Appliance OS and Device Manager
- Cisco Security Manager
- Cisco IPS v6 OS updates
- Cisco IPS v6 signature updates
- Cisco Security Agent Management Center
- Cisco Anomaly Detector
The latestest version can be downloaded from here.
Monday, June 18, 2007
Cisco ASA v8.0 and AnyConnect VPN Client Released!
-Mike
Friday, June 15, 2007
Some of My Favorite Links
Blogs:
- Cisco MARS Blog - A terrific blog operated by Chris from the UK. Chris shares a wealth of knowledge about his MARS experiences in his excellent and detailed posts.
- Network Response - Another terrific blog by Chris. This one is more focused on security offerings from Cisco other than MARS.
- Cisco Blog - A general Cisco blog from JC. Offers some very well written posts about some advanced Cisco networking topics. Gave me the inspiration to start this blog.
Projects (free network sh*t!!):
- Cacti - An amazing open-source project aimed at providing an easy-to-use web interface for graphing a variety of SNMP statisticis. Highly customizable and a very extensive plugin offering available via their forums. I'll soon integrate this into CMPC to provide notification when updates are available.
- IPPlan - Another amazing open-source project. This one aims to provide an architecture to manage IP address tracking and provisioning. If you have any more than 5 subnets... download this and love it. I'll soon integrate this into CMPC to provide notification when updates are available.
- Nessus - Software provides one of the most extensive network threat scanners I have ever dealt with. This used to be very hard to use and configure... but the Windows version is ridiculously easy to configure. I'll soon integrate this into CMPC to provide notification when updates are available.
-Mike
Thursday, June 14, 2007
CS-MARS Package Checker (CMPC) v1.0.0.0 Released
http://www.mediafire.com/?c2wwmbmbzxh
Enjoy and leave feedback!
-Mike
Wednesday, June 13, 2007
CS-MARS Package Checker (CMPC) v1.0.0.0 Upcoming Release
CS-MARS Package Checker (CMPC) v1.0.0.0 readme.txt
Updated June 11, 2007 by Mike
Send all feedback/comments/problems to ****** or let me know on my
blog at http://cs-mars.blogspot.com
WHAT IS CS-MARS PACKAGE CHECKER?
================================
CS-MARS Package Checker (more easily written as CMPC) is a tool to help the
growing user community of the Cisco MARS appliance keep it's rules up-to-date.
It's very basic by design, but wildly useful. It quite simply parses the
required information from an XML configuration file, uses the CCO credentials
to log into cisco.com to check for updated packages, and e-mails the results
to a specified e-mail.
CMPC is current developed as a command line executable. This was easier to port
nearly directly from the first implementation written in PERL under Linux.
Feedback is appreciated on the design, but it is already planned to migrate to
a standard executable.
INSTALLATION
============
The installation of CMPC is rather basic:
- Extract to program archive cmpc.zip. This archive should contain:
- cmpc.exe
- config.xml
- readme.txt
- You may place these files wherever you see fit. The only requirement is that
the cmpc.exe and config.xml are within the same directory. The easiest
location may be something such as C:\CMPC\
CONFIGURING CMPC TO RUN
=======================
Configuration of CMPC for runtime is handled through the included config.xml
configuration file. Open the file in your favorite text editor and fill in all
fields like so:
Please keep in mind that all fields are required. Certain validity checks are
run while CMPC processing, but a majority of issues running this program are
sourced from an incorrect config.xml. Support is always available on my blog
or by e-mailing me at ******.
REMOVAL
=======
Simply remove the directory in which you installed CMPC.
PROBLEMS USING CMPC
===================
CMPC has been developed to catch most exceptions and give informative errors
when issues occur. That being said, errors do occur that I may not catch. If
you are running the cmpc.exe executable from Windows XP, the error output may be hard to catch as the dialog will close after erroring. To solve this, open up
the Windows XP command prompt and run the cmpc.exe executable from there. This should allow you to see the error output. If you receive a cryptic error
message, let me know and I'll debug the code on my side.
CMPC HISTORY
============
Apr 27, 2005 v1.0.0.0
- Initial release.
Saturday, June 02, 2007
CS-MARS Package Checker: Keeping your MARS appliance up to date
CS-MARS, like most security devices, is only as useful as the known threats built into the device. Anyone who operates an IPS/IDS device knows how critical it is to keep such a device up-to-date. CS-MARS is no different. Cisco provides no avenue for automated update checking, so rather than remembering to check CCO every once and a while for package, this program does it all for me, and soon for you.
It's very basic in operation. It was originally written in Perl and ran under Linux, but has since been ported to C# for usability. It's an executable, an XML configuration file, and scheduling is done through Windows (scheduled taks). Simply configure the XML file with your CCO credentials, SMTP server, and the From/To mail account. After then, you can execute the program at your leisure or schedule it through Windows.
Though this may sounds simple, it's a wildly useful tool. It's so useful, I've begun re-writing it to allow checking of other packages. It now e-mails me daily with the latest packages for CS-MARS, Unified Wireless, ASA/PIX images, and WAAS updates. Don't expect the first release to have the feature of checking for updates for other products, but it is a planned add-on for later releases. Input about other products you'd like to see have similar notifications is welcomed. Just add a comment to this post!
I'm bringing up the topic of this app now because I don't want my blog to simply be me throwing up information onto the Internet (though if I drink Jack Daniels... well.. different topic). I want input from anyone that has anything to say. I'm wrapping up development now in my free time, but I'd like to hear input about whether this would be useful or not. Drop a comment or two and expect to see the release in the coming weeks.
Friday, May 25, 2007
Unified Wireless Guest Access: Authenticating Users
- Web Policy - Authentication
- Web Policy - Passthrough
- Web Policy - Conditional Web Redirect
For actual guest user authentication, I'm going to focus on using the "Web Policy - Authentication" option. Using this security policy (as configured under our guest SSID), a guest user is re-directed to login if his/her wireless card has just associated to an open SSID and a browser is opened. This is very similar to setups you see in hotels and airports. For this example we will use the canned authentication scheme that Cisco has designed. This requires that a username and password be created for all guest users. With this username/password combination, he or she will authenticate to the guest SSID and be given guest wireless access for a defined period of time.
The first place to start is with the basic guest authentication screen. This is accessed by clicking Security -> Web Login Page. You can do some basic HTML customization and change titles. Use and abuse the "Preview..." button to make sure it looks like how you would expect. Next... let's take a look at how a guest user is created. Click on Security -> AAA: Local Net Users -> New... Fill out the fields as seen below. Make sure to create the user as a Guest user so you an enable timing out the account. Once the account is created... the user may now login through the guest web portal you designed above.
Sounds like a good plan, right? Well, the issue I take with this is that it requires your receptionists to access a controller to build in a username and password. I'm thinking an easier way would be to provide some front-end to a receptionist to allow him or her to simply enter a username to authorize a users. The guest user then builds his or her own password and provides a company name to be used for authentication. Problem is... this is not how guest access was designed by Cisco and will require some programming on our side. Interested how this is done? Stay tuned for an in-depth view behind how guest users are created and how we can customize a front-end for guest user registration.
Wednesday, March 28, 2007
Unified Wireless Guest Access: Prep'ing the Controller
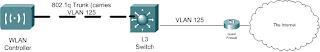
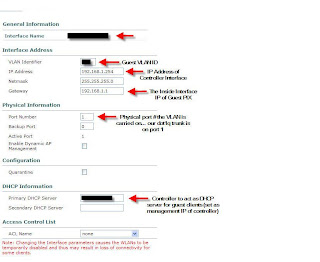
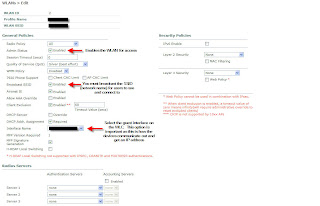
Tuesday, March 27, 2007
Unified Wireless: My Take on Guest Access
Guest Access is pretty much what it sounds like. It's taking your wireless infrastructure and allowing "guest" users to access it while keeping your existing UW infrastructure secure. This could be used to provide Internet access to vendors visiting your facilities, or could go beyond and actually act as a open hotspot for customers. The version of Guest Access I'm working on involves allowing guests at our corporate campus to use our Internet connectivity for presentations/remote VPN access. Our corporate campus is comprised of multiple facilities all linked over our private MPLS VPN cloud.
Let me go a little bit into the architecture behind the implementation. In our headquarters facility we have installed a Cisco 4402 Wireless LAN controller. This controller acts as the "nexus" for our Guest Access infrastructure, along with allowing secure access to internal network resources for mobile employees. Our satellite offices, also part of the corporate campus, are all connected via Cisco 2811 Integrated Services Routers. In these offices we will be using NM-WLC-6 network modules. Essentially these modules are Wireless LAN Controllers which sit on-board ISR routers.
I don't want to get too in-depth with Guest Access this first post. Let me leave with a quick diagram of how I've decided to implement Guest Access. In future posts I'll go into detail as to how this can be implemented. Keep in mind that my implementation may not be the same as yours, but the concepts I use may be shared amongst many implementations.

Thursday, March 22, 2007
CS-MARS v4.2.5(2456) Available!
And in other news...our Clean Access project has been placed on hold to focus resources on a new Cisco Unified Wireless implementation. The budget money was available, so the equipment is here and the system is being developed. The unified wireless system focuses on extending security across your wireless network while enabling services that are normally available to only wired clients. Keep an eye out for details on our implementation... along with some in-depth discussion as to how we'll be handling guest access in the near future.
Tuesday, March 06, 2007
The World of Clean Access
Let me go into a little detail about Cisco Clean Access (CCA) and how it will be used in our environment. CCA is comprised of a Clean Access Manager (CAM) and Clean Access Server (CAS). The CAM dictates all the policies required to gain access to the network, while the CAS handles authentication of workstations and quarantining as necessary. Both are required components of a Clean Access implementation.
During our initial pilot we will be validating workstations from a remote office, along with select users in our headquarters facility. This brings up some issues that can all be solved based upon the CCA implementation that is selected. Now this update is just a brief overview of my most recent project... but expect updates soon about the infrastructure concepts involved in CCA and some of the configuration involved with the project. The resources on Clean Access are limited on the Internet, so I do want to dedicate a portion of this blog to this exciting product. Continue to expect updates about CS-MARS... along with other Cisco security updates.
-Mike
Friday, February 16, 2007
CS-MARS 4.2.4 Released!
Just a quick note letting everyone know that CS-MARS v4.2.4 has been released. The most important update is for those of us under stress about the upcoming DST change.:
Support for Extended Daylight Savings Time. On March 11, 2007, the United States will adjust to Daylight Saving Time (DST) three weeks earlier than previous years and will end one week later on November 4, 2007. As per the Energy Policy Act of 2005, MARS supports this change in 4.2.4.
Wednesday, February 07, 2007
Security News: Cisco Update Security Portfolio
- Adaptive Security Appliance v8.0
- Cisco IPS v6.0
- Cisco Security Agent v5.2
- CS-MARS v4.3
- Cisco Security Manager v3.1
As you can see nearly every product that is part of the "Self-Defending Network" is being enhanced to support this tighter integration. Of big note is the ASA v8 release, with numerous enhancement to the SSL VPN capabilities of the ASAs. SSL VPN is the next generation of secure remote network access. Below are these enhancements. Note that a new VPN client is to be released... known as "AnyConnect." This appears to be the Cisco-supported Vista VPN client that will be used going forward.
- Clientless VPN with enhanced portal design for highly customizable user experience including personalized bookmarks, RSS feeds, and localization support.
- Cisco's next-generation "AnyConnect" VPN client, with broader operating system support for Microsoft Vista and Windows, MAC OS X, and Linux.
- Cisco AnyConnect Mobile VPN client supports Windows Mobile 5.0 Pocket PC Edition.
- Optimized network access for voice over IP (VoIP) and other latency-sensitive traffic.
- Ability to create "smart tunnels" that provide policy-driven applications specific access without requiring administrative rights.
- Embedded Certificate Authority (CA) and additional user credential options simplify authentication.
- Direct mapping of Windows Active Directory membership to VPN access simplifies IT's security management by automatically granting users appropriate VPN permissions.
- Posture-assessment extensions adjust users' VPN permissions more efficiently.
- Intuitive management via ASA's Adaptive Security Device Manager, CSM 3.1.
Note that the full press release can be found here. It looks like some exciting changes are happening with Cisco's security portfolio. Make sure to check in for the latest updates as I get them.
Tuesday, January 16, 2007
IPS Troubleshooting: "The root element is required in a well-formed document"
ERROR 13:42:28 [main] - (Log.java:198) - IPS-TEST -SensorConfigImportcaught: Unable to import sensor config using RDEP: java.lang.Exception: An exception occurred during the import of file(null), detail=Error on line 1 ofdocument : The root element is required in a well-formed document.
And for those that are seeing the error... this is what the "status messages" dialog shows:

So now what? What does this mean and how do I get my sensors to import without this issue? The error is Cisco's fault and not yours (I know *snicker* *snicker*). The issue is that the latest version of IPS MC cannot parse the configuration of the sensor due to the addition of the V, which is the anti-virus update version (as seen in the sensor version in the above dialog). This bug is found under CSCsh11502. The workaround as presented by Cisco is:
Well.. I know the next thing that I thought was that re-formating the sensor and then doing the update via the IPS MC was just a tremendous waste of time. How do you get around it? Open up a TAC case with Cisco and ask for the "CSM301SP1_Patch.zip" fix for this issue. Once I patched my CSM 3.01 install I was able to import and update. All together this took nearly a month of investigating and going back-and-forth with TAC about this issue. I hope this info can help anyone else that runs into this come to a quicker resolution. As always, questions are welcomed and comment appreciated.Downgrade the sensor to an earlier version that does not have the V version in it. Then use the IPSMC to upgrade to the current version.
-Mike
He's Back!
I hope everyone had a good holiday. I've been so busy that I've lost track of keeping up-to-date with this. But I see there's still plenty of interest... this site still receives over 100 hits a day. So what's been new an exciting in the world of Cisco security? Let's take a look:
+ CS-MARS Updated to 4.2.3 (2403) - This latest update updates vendor signatures along with enhancements to SSL/SSH fingerprint change detection. See the release notes on cisco.com here.
+ IPS 6.0 Released - Definitely some big news for IPS 4200-series & IDSM-2 sensors users. IPS 6.0 has been release for download for users with an IPS Services contract. IPS 6.0 includes many enhancements that are outlined below (right from cisco.com). I'd like to note that users should continue to wait on upgrading to IPS 6.0 until it is fully integrated with existing management products. As of now CS-MARS is not updated to support the new 6.0 fields and current IPS MC (centralized IPS management console provided by CSM or CiscoWorks VMS) cannot be used to manage 6.0 senors. No need to rush... as tempted as we all are:

+ Cisco Security Manager to Replace CiscoWorks VMS - In what I believe is a great move (but may be frowned on by others), VMS (VPN Management System) is to be replaced with the newest security device management product from Cisco, Cisco Security Manager (CSM). I've worked on both and can say from a management standpoint this change is excellent. CSM includes CSM client to manage PIX and ASA devices centrally, IPS MC to manage all IPS sensors and push updates out from a central repository (really a terrific product), and Resource Manager Essentials. I plan to give a tour of each of the CSM product in an upcoming update to show what it has to offer. It has come under scrutiny as it does not include Security Monitor. Instead, CSM integrates directly with CS-MARS so incident detection can include policy lookups to the CSM server.
I hope this update is proof that I'm still alive and keeping busy. I have enjoyed the wonderful comments everyone has left and am impressed with the talent shared by everyone in the discussions.
-Mike
