Saturday, October 07, 2006
Important CS-MARS Update!
With the release of 4.2.2 I had updated our production MARS system to the latest code. Upon doing so the system began to repeatedly crash while adding devices and developing new rules. Cisco has released a patch for this bug to bring MARS from 4.2.2 (2302) to 4.2.2 (2303). The patch is available here to download. Even if you are not seeing issues I recommend you update your MARS appliance to this latest revision of code to prevent issues in the future.
Monday, October 02, 2006
Cisco News: The New Cisco.com Unveiled!
On today, October 2nd, Cisco has officially unveiled the new Cisco.com. The new website boasts improved navigation, a more modern design, a new logo, along with the ability to access the site from a mobile device at www.cisco.mobi. Too bad the NetPro forums haven't been updated with the new design...
Friday, September 29, 2006
CS-MARS Title Available at Cisco Press!
Hey again everyone! In keeping with trying to bring the most information about MARS that I have I thought I'd share a new resource. I own a slew of Cisco Press titles on everything from CCNA guides to MPLS network design titles. Now available at Cisco Press is a book on MARS... Security Threat Mitigation and Response: Understanding Cisco Security MARS. I'd highly recommend this text to anyone that uses a CS-MARS appliance. I do not own the title but can speak highly on the level of detail I've found in all Cisco Press titles. You can grab a copy here and make sure to sign up for Cisco Press... it's free and you can get all titles for the member price.

Tuesday, September 26, 2006
CS-MARS v4.2.2. Now Available!
Just as I was about to finish a new post I received notifcation that v4.2.2 of CS-MARS is now available from CCO. Go download it and make sure to check out the release notes.
Sunday, September 24, 2006
CS-MARS Rule: IOS Login Auditing
I'm back! Sorry for the short break... it's been rather busy around here. So now we've done an introduction about CS-MARS and seen how to get Windows servers logging events. Let's now take a look at creating a rule for our IOS network devices. This first rule we'll design (it actually can be customized into many rules) will allow us to generate incidents whenever a user succeeds or fails login to a monitored IOS device (switch, router, IOS AP, etc...). Start by reading this document at Cisco. Starting with IOS version 12.3(4)T we have the option of generating syslog messages when a user fails or succeeds login to the device. The important commands are:
login on-failure log
login on-success log
login block-for seconds attempts tries within seconds
Now let me briefly talk about the last command. This allows the IOS device to protect it's vty port by dynamically creating an ACL to block the IP that has failed times withing for a configurable amount of . As an example we use login block-for 180 attempt 3 within 60 on all of our IOS devices. With this configured, when I now login to a device a syslog message is generated and forwaded to our MARS server that looks like this:
Sep 25 13:48:58 EDT: %SEC_LOGIN-5-LOGIN_SUCCESS: Login Success [user: marsguy] [Source: 10.27. 1.11] [localport: 22] at 13 :48:58 EDT Mon Sep 25 2006
And if I fail login (which surely never happens!) it would look like this:
Sep 25 13:52:29 EDT: %SEC_LOGIN-4-LOGIN_FAILED: Login failed [user: ] [Source: 10.27.1.11] [localport: 22] [Reason: Login Authentication Failed] at 13:52:29 EDT Mon Sep 25 2006
Now we have some pretty nifty message... let's write a rule in MARS to generate incidents on successful and failed l ogins. Let's start with successful logins. I took a screenshot of this rule as we have it written. We have some customizations so we don't get notified whenever our CiscoWorks server logs in (it's a chatter box!). Obviously this can be tuned by just looking at how I have ours tuned and customizing it for your infrastructure.

And here's a look at our failed login attempt rule. Again... edit the customizations to fit your environment:
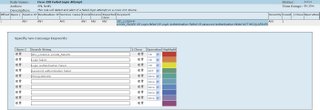
I hope this was a good example of some basic rule writing I've done with our MARS system. Any questions on how these rules are implemented please let me know and I can help.
login on-failure log
login on-success log
login block-for seconds attempts tries within seconds
Now let me briefly talk about the last command. This allows the IOS device to protect it's vty port by dynamically creating an ACL to block the IP that has failed
Sep 25 13:48:58 EDT: %SEC_LOGIN-5-LOGIN_SUCCESS: Login Success [user: marsguy] [Source: 10.27.
And if I fail login (which surely never happens!) it would look like this:
Sep 25 13:52:29 EDT: %SEC_LOGIN-4-LOGIN_FAILED: Login failed [user: ] [Source: 10.27.1.11] [localport: 22] [Reason: Login Authentication Failed] at 13:52:29 EDT Mon Sep 25 2006
Now we have some pretty nifty message... let's write a rule in MARS to generate incidents on successful and failed l

And here's a look at our failed login attempt rule. Again... edit the customizations to fit your environment:

I hope this was a good example of some basic rule writing I've done with our MARS system. Any questions on how these rules are implemented please let me know and I can help.
Wednesday, August 09, 2006
Q&A: How does MARS work with Windows Event Logs?
This questions was posed by Jesmond Psaila in Australia:
This is an excellent question. Since I teach by example I'll show how this is done with an example. In this example we're going to take a Windows 2000 server (SP4 loaded) and have it log login failure and successes to the MARS appliance. We'll even create our own rules to trigger notification of login failures and successes. There's two techniques of getting logs onto the MARS appliance: push and pull. Here I'll be using the "pull" function, in which MARS will log into the server and poll the event log. I prefer this over placing SNARE on all servers and "pushing" the logs to MARS. This mini-tutorial make the assumption you have a base understanding of Windows server administration.
1) Configure your Windows 2000 Server to log login events:
I could sit here an explain this... but Microsoft has a brief tutorial on this. You can find it here. Below is a screenshot of my console after logging is fully enabled. If you view your Security Event Viewer now you should see login/logout events:

2) Configure CS-MARS to pull events from the Windows 2000 Server
Login to your MARS appliance and go to Admin -> Security and Monitor Devices -> Add. Now choose "Add SW security apps on new host." The screen should now look like this:
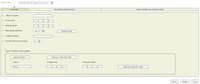
Fill in all fields and make sure to choose "Windows" Operating System. Then click the "Logging Info" button to choose your event polling options:
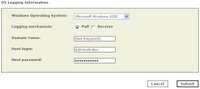
After this you can click "Done" and the device should be added. Make sure to "Activate" it in the upper-right hand corner.
3) As an aside you can configure how often MARS will go out and poll for events on the configured servers. This is found under Admin -> System Parameters -> Windows Event Log Pulling Time Interval. I use 60 seconds:

4) Next I like to always verify that logging is properly working.
Let it run for about 10-20 minutes (good time to go grab a coffee) and come back and pull the raw events from MARS. To do this go to Admin -> System Maintenance -> Retrieve Raw Messages. I usually like to go back 10 minutes or more. Fill out the option like below and make sure to select just your Windows 2000 server (mine's named CISCOWORKS). Then click Submit.
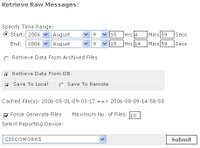
5) After you have verified that you see messages... now you want incidents to be created when triggered events happen. I've created an example rule that will create an incident when a user logs into the server. Here's the details on it:
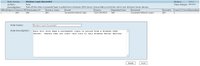
Obviously you can tweak this as you must. Find the keywords in the raw messages and use those as a "Keyword" to fire off incidents.
I hope this helped explain how to get Windows Servers logging with MARS and generating rules to fire events for server logins. Though this was done to help Jesmond, anyone with any questions or that would like more example rules please let me know.
Hi Mike,
I think you have a pretty cool blog. My name is Jes I work for a Cisco Gold Partner in Australia. I am focusing on Cisco Security at the time being. I have deployed a couple of MARS deployment mainly using network device for reporting agent.
I notice you have some Windows Servers reporting to your MARS.
I am working on a current opportunity where the customer would like MARS to report on sucessfull and unsucessfull logins for Windows users.
I know that Win Eventlogs capture this. with the use of a SNARE agent can I get MARS to provide an aggregate report of this login activity.
Regards
Jesmond Psaila
This is an excellent question. Since I teach by example I'll show how this is done with an example. In this example we're going to take a Windows 2000 server (SP4 loaded) and have it log login failure and successes to the MARS appliance. We'll even create our own rules to trigger notification of login failures and successes. There's two techniques of getting logs onto the MARS appliance: push and pull. Here I'll be using the "pull" function, in which MARS will log into the server and poll the event log. I prefer this over placing SNARE on all servers and "pushing" the logs to MARS. This mini-tutorial make the assumption you have a base understanding of Windows server administration.
1) Configure your Windows 2000 Server to log login events:
I could sit here an explain this... but Microsoft has a brief tutorial on this. You can find it here. Below is a screenshot of my console after logging is fully enabled. If you view your Security Event Viewer now you should see login/logout events:

2) Configure CS-MARS to pull events from the Windows 2000 Server
Login to your MARS appliance and go to Admin -> Security and Monitor Devices -> Add. Now choose "Add SW security apps on new host." The screen should now look like this:

Fill in all fields and make sure to choose "Windows" Operating System. Then click the "Logging Info" button to choose your event polling options:

After this you can click "Done" and the device should be added. Make sure to "Activate" it in the upper-right hand corner.
3) As an aside you can configure how often MARS will go out and poll for events on the configured servers. This is found under Admin -> System Parameters -> Windows Event Log Pulling Time Interval. I use 60 seconds:

4) Next I like to always verify that logging is properly working.
Let it run for about 10-20 minutes (good time to go grab a coffee) and come back and pull the raw events from MARS. To do this go to Admin -> System Maintenance -> Retrieve Raw Messages. I usually like to go back 10 minutes or more. Fill out the option like below and make sure to select just your Windows 2000 server (mine's named CISCOWORKS). Then click Submit.

5) After you have verified that you see messages... now you want incidents to be created when triggered events happen. I've created an example rule that will create an incident when a user logs into the server. Here's the details on it:

Obviously you can tweak this as you must. Find the keywords in the raw messages and use those as a "Keyword" to fire off incidents.
I hope this helped explain how to get Windows Servers logging with MARS and generating rules to fire events for server logins. Though this was done to help Jesmond, anyone with any questions or that would like more example rules please let me know.
Wednesday, July 26, 2006
Making the Shoe Fit - CS-MARS Sizing
So you want a MARS box but don't know which one to buy? Cisco offers many options as to which appliance you can purchase and even has details online as to how each appliance is sized.

So as you can see the sizing is based upon events per second. So how excactly can you measure you events per second? Let me clarify this by showing you the devices we monitor and all together the events per second we generate. Here' our monitored devices:
4 x Windows Server
121 x Cisco 2811 IOS Routers
384 x Cisco 3750 IOS Switches
117 x PIX 506E Firewalls
2 x PIX 520 Firewalls
2 x PIX 515E Firewalls
7 x Cisco 3825/3845 Routers
2 x Cisco 4215 IPS 5.1 Sensors
6 x Unix Servers with Snort
So all together we have a relatively large infrastructure monitored by MARS. So events per second comes to what excactly? At peak usage during the day we generate about only 57 events per second. Which CS-MARS version do we run? We're currently running the 100e, which is capable of 3000 events per second! Wow... that's pretty damn powerful! We bought this size knowing that our infrastructure will soon include more servers along with NAC reporting to MARS. Hopefully this sizing overview helps when making the decision to purchase a CS-MARS appliance. If you ever need any help or recommendations, just ask!

So as you can see the sizing is based upon events per second. So how excactly can you measure you events per second? Let me clarify this by showing you the devices we monitor and all together the events per second we generate. Here' our monitored devices:
4 x Windows Server
121 x Cisco 2811 IOS Routers
384 x Cisco 3750 IOS Switches
117 x PIX 506E Firewalls
2 x PIX 520 Firewalls
2 x PIX 515E Firewalls
7 x Cisco 3825/3845 Routers
2 x Cisco 4215 IPS 5.1 Sensors
6 x Unix Servers with Snort
So all together we have a relatively large infrastructure monitored by MARS. So events per second comes to what excactly? At peak usage during the day we generate about only 57 events per second. Which CS-MARS version do we run? We're currently running the 100e, which is capable of 3000 events per second! Wow... that's pretty damn powerful! We bought this size knowing that our infrastructure will soon include more servers along with NAC reporting to MARS. Hopefully this sizing overview helps when making the decision to purchase a CS-MARS appliance. If you ever need any help or recommendations, just ask!
Monday, July 24, 2006
A Visual Intro to CS-MARS
So what is CS-MARS and why does it deserve a blog? CS-MARS (short for Cisco Security Monitoring, Analysis and Response System) is a security aggregation point for network devices. I could sit here and talk about all the blah blah that the PDFs on Cisco.com provide, but I think a visual tour of our implementation of MARS will best describe this powerful network security tool.
1) Incident Dashboard - The CS-MARS homepage for events. Shows the 5 most recent secuirty events along with daily statistics and brief security diagrams.

2) Incident Listing - Here we see the most recent Incidents as recorded by MARS. You get all the basic information on the Incident triggered, and from here you drill into specific Incidents.
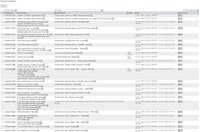
3) Rule View - Here we can see the rules the come built-into the MARS system. There are current 124 system rules. This sounds very minimal, but think of rules as the aggregation of multiple events (which we'll see soon). Rules are what generate incidents and can notify us.
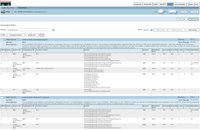
4) Event View - Here is where we see the invidual events that MARS recognizes coming from devices. As of version 4.2.1 there are over 16,000! These are the events that are triggered from logs/polling of the monitored devices. The events are then correlated to the above rules and grouped to form incidents that represent security events.
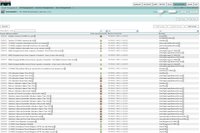
5) Incident Details - On the final part of this tour I'll drill into a specific incident. Here we see a supposed VPN attack that was successful. This was the result of a user, christine, failing login to our VPN endpoint, disconnecting, then connecting succesfully. MARS detects this as a successful VPN password attack and generates an incident. As a network engineer I know this is a real user and that this incident is the result of a user mistyping credentials. In the event this user was not a real user, we would have an incident to now investigate further.

I hope this introduction showed how much power is behind this appliance. It's been a really exciting system to work on and I'm constantly learning more and more about the true capabilities of it. Now if I can just make it take my off-hour calls I'll be one happy network engineer...
1) Incident Dashboard - The CS-MARS homepage for events. Shows the 5 most recent secuirty events along with daily statistics and brief security diagrams.

2) Incident Listing - Here we see the most recent Incidents as recorded by MARS. You get all the basic information on the Incident triggered, and from here you drill into specific Incidents.

3) Rule View - Here we can see the rules the come built-into the MARS system. There are current 124 system rules. This sounds very minimal, but think of rules as the aggregation of multiple events (which we'll see soon). Rules are what generate incidents and can notify us.

4) Event View - Here is where we see the invidual events that MARS recognizes coming from devices. As of version 4.2.1 there are over 16,000! These are the events that are triggered from logs/polling of the monitored devices. The events are then correlated to the above rules and grouped to form incidents that represent security events.

5) Incident Details - On the final part of this tour I'll drill into a specific incident. Here we see a supposed VPN attack that was successful. This was the result of a user, christine, failing login to our VPN endpoint, disconnecting, then connecting succesfully. MARS detects this as a successful VPN password attack and generates an incident. As a network engineer I know this is a real user and that this incident is the result of a user mistyping credentials. In the event this user was not a real user, we would have an incident to now investigate further.

I hope this introduction showed how much power is behind this appliance. It's been a really exciting system to work on and I'm constantly learning more and more about the true capabilities of it. Now if I can just make it take my off-hour calls I'll be one happy network engineer...
Saturday, July 22, 2006
Mobile Messaging Using the Sprint PPC-6700
Eat this Blackberry! In a company that's pretty large (25,000+ employees), we have an under-staffed IT department. Surprising right? Anyways, when the CS-MARS device was installed we started receiving the built-in e-mail alerts about security events. The issue was that we had no mobile devices to receive the alerts on. Though the e-mail alerts are pretty cheesy, but I have a notification enhancement I'll share on one of these posts (all written in a network engineer's favorite language Perl). So with my large paycheck (pfft!) I purchased a Sprint PPC-6700. This is everything a Blackberry is and more. We're in the process of an MS Exchange 2003 migration and thanks to our awesome Windows admin, he configured Microsoft DirectPush e-mail. This means that the Blackberry "push" functionality is built-in to my device and our new mail environment. I now receive alerts as they occur and can more easily respond to them. Plus it's a cool phone everyone is jealous of. If we could only get EVDO coverage up here!




Friday, July 21, 2006
An Introduction
A brief introduction of who I am and what I do. My name's Mike and I'm a Cisco-certified network engineer. I'm 22 years old and have worked on networks for the past 5 years. I current works in the private sector as a Network Engineer for a local food retailer. We are based in 6 states in the Northeast. My responsibilities include maintaining the operation of our MPLS network, along with investigate new technologies to enhance services on our network. My main focus now is business continuity connectivity along with investigating the newest network security technologies. My primary focus has been the installation and operation of the Cisco CS-MARS security event manager. This robust product offers a lot, but I find that Cisco falls short on providing an in-depth view of the power of the device and how it benefits any company that operates a secure network. My hope is that this blog will provide insight into the security technologies offered by Cisco, with a focus on the CS-MARS device. Along the way I'll share my experiences in networking and hopefully hear input for fellow engineers out there.


Subscribe to:
Posts (Atom)